Your smartphone is probably one of the most important tools in your daily life. It helps you stay connected, entertained, and organized. But let’s be real—smartphones aren’t cheap, and replacing one every couple of years can hurt your wallet. The good news? With a little care, you can make your phone last longer. Here are five easy tips to keep your smartphone running like new.
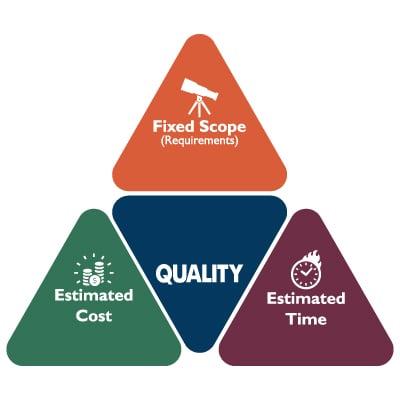
There is a concept known as the iron triangle that provides a simple framework for project management by outlining the balance between your costs, your available time, and the desired quality of your outcome. Traditionally, the iron triangle helps illustrate how these factors impact each other. Instead, we wanted to take advantage of the principles of the triangle to explore how beneficial it can be to outsource IT services.
Happy New Year! This time is usually dedicated to making plans and commitments to improve oneself over the coming months in the interest of the future. In the spirit of the holiday, let’s talk about how the right resolutions can help your career or your business’ use of technology.
Since so much of the world is now online, businesses and organizations interact with people online now more than ever. This means they also collect people’s information, a practice they do for various reasons. Individuals need to consider their own data privacy and how it might be affected by business practices.
Computer problems can be super frustrating, especially when they slow you down while working. Many times, it is something that can be fixed quickly, but then there are issues that an experienced IT professional has to address. Let’s take a look at some of the most common computer problems professionals run into.