Recent Blog Posts
What are the Benefits of Automation? Automation provides many opportunities to streamline operations, particularly simple tasks that can allow companies to focus their attention on other more lucrative endeavors. Here are some of the benefits that can come from automating these tasks:
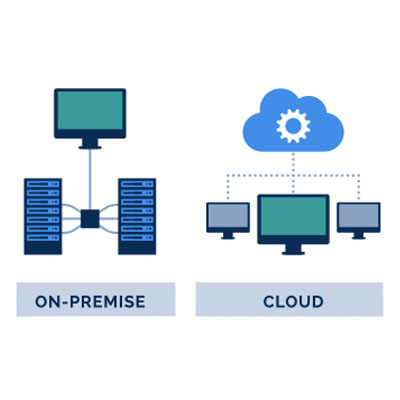
The Big Difference The biggest difference between on-site hard drives and cloud computing is that hard drives are connected to your central infrastructure. Many companies find they prefer to have direct control and access to their data storage by hosting it on-site, and this has the added benefit of your IT department having quick and immediate access to the infrastructure in the event the drives are rendered inoperable. Of course, this also means that businesses using on-site storage have to maintain and manage it themselves, which translates to additional utility costs, salaries for technicians, and storage space. This is all before you include the data backup itself.
How Much Should I Spend On My Business? Cybersecurity? If you were hoping to get a set dollar amount, I?m sorry to disappoint you. Generally speaking, small and medium-sized businesses spend an average of anywhere from 5% to 20% of their entire information technology budget on their cybersecurity, with the average IT budget hovering around 4% of their overall budget.
Remote Work Remote work saw an explosive rise in popularity a few years ago, and there were significant environmental impacts associated with this rise?and why wouldn?t there be? With people no longer needing to commute to the office to do work, a significant volume of emissions were removed from the equation. Continuing to do so will allow these decreases to continue to some degree.
What is Habit Stacking, Anyways? Think about the little things that you do while at work, each and every day, all the parts of your routine that have become automatic. You don?t really have to think about them, do you? At this point, it?s just what you do. You probably have a few things like this in your personal life, too? things and processes that feel so natural at this point that not doing them feels wrong.